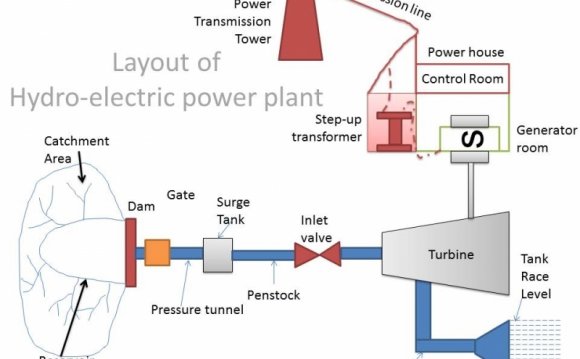
I. I NTRODUCTION development of this Supervisory Control and Data Acquisition (SCADA) systems features in the earlier ten years created a considerable issue with respect to their particular protection. Cause of their weaknesses to different forms of cyber- assaults include the following: (1) utilization of available communication standards, (2) connectivity of the control methods along with other networks, (3) limitations into the existing safety technologies, (4) remote access, and (5) option of technical information about control methods. Since the safety of SCADA systems is of high relevance because of their vital part on the market, that is a present field of analysis aided by the hope of certain solutions for security and information security risk management. A secure ICT system should, as a whole, give you the following, by order of priority: confidentiality, integrity and supply. Industrial remote tracking and control systems have a similar safety demands, in a reversed order. The path to the fulfilment of the protection needs dictates the adoption of a security policy that plainly describes laws, business process protocols, staff functions, permissible activities, actions and processes [1], [2]. Regulations determine means of protecting the stability of the information, determine the privacy of information, information availability, along with the accessibility control of sources and programs. ICT systems when you look at the electric power resources have to meet high standards with regards to dependability, supply and transfer of proper and prompt information when it comes to functions of production preparation, efficient usage of the vitality possible, remote management in manufacturing, transmission and distribution places, reporting and effective company handling of the system as a whole. Through the remote administration aspect, measuring, control and management of the electric power manufacturing in hydroelectric power flowers, SCADA has a central part. Fig. 1 shows a block drawing of SCADA implementation centered on stand-alone principles. These types of principles enable the highest dependability degree of the production cycle because in instance of an outage of every associated with production-transfer devices, generator-transformer, the areas and all various other production-transfer units remain in manufacturing cycle undeterred. The ICT structure of these devices is enjoined into one synergy in the standard of SCADA systems. Modern-day telecommunication methods promoting SCADA count on online protocol (internet protocol address) and Ethernet technologies. SCADA-specific protocols are now being created in the application layer (including information models and presentation) and use the internet protocol address protocol stack. SCADA systems are generally incorporated into a common IP-based network, together with the other working and business telecommunication solutions. Companies therefore designed have specific weaknesses
Source: www.researchgate.net